
In an era where our virtual interactions are as frequent as our physical ones, ensuring robust safeguards for our digital identities becomes paramount. This section delves into strategies and tools that go further than conventional measures, offering a comprehensive approach to maintaining your anonymity and integrity in the digital realm.
Understanding the Landscape: As technology evolves, so do the methods employed by those seeking to exploit vulnerabilities. This article explores the advanced techniques and philosophies that can fortify your defenses against a spectrum of threats, from data breaches to sophisticated phishing attempts.
Beyond Basic Protection: While basic security protocols are essential, they often fall short in the face of increasingly complex cyber threats. Here, we will guide you through the implementation of more sophisticated security measures, ensuring that your digital footprint remains secure and untraceable.
Understanding Advanced Encryption Techniques
This section delves into the sophisticated methods used to protect information from unauthorized access. Encryption, a cornerstone of data protection, involves transforming readable data into a format that can only be deciphered with the correct key. As technology evolves, so do the techniques to ensure that sensitive information remains secure against increasingly sophisticated threats.
Advanced encryption techniques are crucial in today’s digital landscape. They provide a robust layer of defense against cyber threats by transforming data into complex codes that are nearly impossible to decipher without the appropriate decryption keys. These techniques are not only more secure but also more efficient, ensuring that data integrity and confidentiality are maintained without compromising speed or accessibility.
One of the most prominent advanced encryption methods is the use of asymmetric cryptography, also known as public key cryptography. This method involves two keys: a public key, which is accessible to anyone, and a private key, which is kept secret by the owner. Data encrypted with the public key can only be decrypted with the corresponding private key, ensuring that only the intended recipient can access the information. This method is widely used in secure communications, including email encryption and secure web browsing.
Another significant advancement in encryption is the development of quantum cryptography. This emerging field leverages the principles of quantum mechanics to secure data transmission. Quantum keys, once observed, change their state, alerting the sender and receiver to any potential interception. This technology promises to revolutionize secure communication by providing a level of security that is theoretically impervious to hacking by current means.
In conclusion, understanding and implementing advanced encryption techniques is essential for safeguarding sensitive information in the digital age. As threats continue to evolve, so must our defenses. By embracing these sophisticated methods, we can ensure that our data remains protected against even the most advanced cyber threats.
The Role of Two-Factor Authentication in Enhancing Security

Introduction: In the realm of safeguarding personal and corporate data, a pivotal strategy stands out for its effectiveness in bolstering protection levels. This section delves into the intricacies of a method that significantly enhances the robustness of access controls, ensuring that only authorized individuals can gain entry into sensitive systems.
Understanding Two-Factor Authentication: Two-factor authentication (2FA) is a security protocol that requires users to provide two different authentication factors to verify themselves before gaining access to a resource such as an application, online account, or a network. This approach goes beyond the traditional single-factor authentication, which typically involves only a password. By incorporating an additional layer of verification, 2FA significantly reduces the risk of unauthorized access, even if the primary password is compromised.
Types of Authentication Factors: The three common types of authentication factors used in 2FA are something you know (like a password), something you have (such as a smartphone or a security token), and something you are (biometrics like fingerprints or facial recognition). Combining any two of these factors enhances the security of the authentication process, making it more resilient against attacks.
Implementation and Best Practices: Implementing 2FA involves integrating it into the existing security infrastructure. It is crucial to ensure that the implementation is user-friendly to encourage widespread adoption. Best practices include educating users about the importance of 2FA, selecting reliable authentication apps or tokens, and regularly reviewing and updating the 2FA setup to adapt to emerging threats.
Challenges and Solutions: Despite its benefits, 2FA can face challenges such as user inconvenience, potential for device loss or theft, and the need for continuous updates to stay ahead of sophisticated hacking techniques. Solutions to these challenges involve simplifying the user experience, implementing backup options for lost devices, and staying vigilant about the latest security developments to enhance the resilience of the 2FA system.
Conclusion: In conclusion, two-factor authentication plays a crucial role in enhancing security by adding an extra layer of protection to access controls. By understanding and implementing 2FA effectively, organizations and individuals can significantly mitigate the risks associated with unauthorized access, thereby protecting valuable data and resources.
Exploring Secure Browsing Practices
In this section, we delve into the essential strategies that enhance the safety of internet navigation. Understanding and implementing these practices can significantly reduce the risks associated with online activities, ensuring a more protected and private experience.
To begin with, it is crucial to employ a combination of tools and behaviors that fortify your browsing against various threats. Here are some key practices:
- Use of Secure and Updated Browsers: Always ensure that your web browser is up-to-date. New updates often include security patches that protect against known vulnerabilities.
- Adoption of Anti-Malware Software: Equip your device with reliable anti-malware software. This software helps detect and remove malicious programs that could compromise your system.
- Enable Browser Security Features: Features like pop-up blockers and secure DNS can prevent unwanted intrusions and enhance your browsing security.
- Be Cautious with Downloads: Avoid downloading files from untrusted sources. Always scan files with anti-malware software before opening them.
- Use HTTPS: Whenever possible, use websites that employ HTTPS protocol, as it encrypts the data between your browser and the website, making it harder for third parties to intercept.
Furthermore, being aware of common online threats is equally important. Here are some threats to watch out for:
- Phishing Attacks: These involve fraudulent attempts to obtain sensitive information by disguising as a trustworthy entity in digital communications.
- Drive-by Downloads: Malware that installs itself on your device simply by visiting a compromised website, without any interaction required.
- Man-in-the-Middle Attacks: This type of attack occurs when a malicious actor intercepts communications between two parties without their knowledge.
By integrating these practices into your daily browsing habits, you can significantly enhance your online safety and protect your personal information from potential threats.
The Impact of AI on Cyber Threat Detection
In the evolving landscape of cyber defense, artificial intelligence (AI) plays a pivotal role. This section delves into how AI technologies enhance the capability to identify and respond to threats in real-time, offering a robust shield against the ever-growing sophistication of cyber attacks.
AI algorithms are designed to analyze vast amounts of data and identify patterns that might indicate malicious activity. By learning from past incidents, these systems can predict and prevent future attacks more effectively than traditional security measures. The integration of AI in threat detection not only speeds up the process but also improves accuracy, reducing Get the full article on Medium likelihood of false alarms.
| Aspect | Description | Impact |
|---|---|---|
| Machine Learning | Utilizes algorithms to learn from data and improve over time without explicit programming. | Enhances the ability to detect anomalies and new threats. |
| Real-Time Analysis | AI systems can process data instantaneously, providing immediate insights into potential threats. | Enables faster response times, minimizing potential damage. |
| Predictive Analytics | Uses historical data to forecast future threats and vulnerabilities. | Helps in proactive security measures, preempting attacks. |
Moreover, AI’s role in cyber threat detection extends beyond mere identification. It also aids in the development of countermeasures, automating responses to neutralize threats. This automation not only saves time but also frees up security personnel to focus on more complex tasks, thereby optimizing the overall security strategy.
In conclusion, the integration of AI into cyber threat detection is not just an enhancement but a necessity in the current digital era. As threats continue to evolve, so must our defenses, and AI stands at the forefront of this evolution, providing the tools necessary to keep pace with cyber adversaries.
Strategies for Managing Digital Identities
In the realm of personal and professional interactions, the effective management of one’s digital persona is paramount. This section delves into the multifaceted approaches that can be employed to ensure that one’s online presence is both secure and reflective of their true identity. By exploring various tactics and tools, individuals can enhance their control over how they are perceived and protected in the digital landscape.
Managing one’s digital identity involves a series of strategic steps that can help safeguard personal information and maintain a consistent online presence. Here are some key strategies:
- Consistent Use of Credentials: Utilizing a uniform set of login details across various platforms can streamline the management process. However, it is crucial to ensure that these credentials are strong and unique to each service to prevent unauthorized access.
- Regular Auditing of Online Profiles: Periodically reviewing and updating profiles on social media and other platforms can help in controlling the narrative of one’s digital identity. This includes removing outdated information and ensuring that only appropriate content is visible.
- Implementation of Privacy Settings: Most online services offer privacy settings that allow users to dictate who can view their information. Taking advantage of these settings can significantly enhance the protection of one’s digital identity.
- Use of Reputation Management Tools: There are various tools and services available that can help monitor and manage one’s online reputation. These can be particularly useful for professionals and businesses looking to maintain a positive digital presence.
- Education on Identity Theft Prevention: Understanding the signs of identity theft and knowing how to respond can be crucial in protecting one’s digital identity. This includes being aware of phishing attempts and knowing how to report suspicious activities.
By adopting these strategies, individuals can take proactive steps towards managing their digital identities effectively. It is an ongoing process that requires vigilance and adaptation to the ever-changing digital environment.
The Importance of Regular Software Updates
In the realm of maintaining robust protection and optimal functionality of our digital tools, regular updates play a pivotal role. This section delves into the intricacies of managing virtual private networks (VPNs), exploring how these complex systems can be navigated effectively to enhance overall safety and efficiency.
Virtual private networks (VPNs) are essential tools for safeguarding online activities and data. However, their effective use requires a deep understanding of their configurations and capabilities. This understanding is crucial as it directly impacts the security and privacy of users. Below, we explore key aspects of VPN management, including setup, maintenance, and troubleshooting.
| Aspect | Description | Importance |
|---|---|---|
| Setup | Initial configuration of the VPN, including server selection and protocol settings. | Ensures the VPN operates correctly and securely from the outset. |
| Maintenance | Regular checks and updates to the VPN software and settings. | Helps in maintaining the integrity and security of the VPN over time. |
| Troubleshooting | Addressing issues that arise with the VPN’s performance or security. | Aids in resolving problems quickly, minimizing potential security risks. |
Understanding these elements not only enhances the user’s ability to manage their VPN but also ensures that they can adapt to new challenges and threats in the digital landscape. Regular updates and proper configuration are key to leveraging the full potential of VPNs for enhanced privacy and security.
Navigating the Complexities of VPNs
In this section, we delve into the intricate world of Virtual Private Networks, exploring their fundamental role in enhancing internet usage. VPNs are not just tools for anonymity but are pivotal in securing data transmission across public networks.
Understanding VPNs: A Virtual Private Network (VPN) extends a private network across a public network, enabling users to send and receive data as if their computing devices were directly connected to the private network. This technology is crucial for encrypting internet traffic and masking the user’s IP address, thereby providing a layer of privacy and security.
Encryption and Anonymity: One of the primary functions of a VPN is to encrypt data, making it unreadable to anyone who intercepts it. This encryption process ensures that even if data is intercepted, it remains secure and confidential. Additionally, by masking the IP address, VPNs offer anonymity, making it difficult for third parties to track online activities.
Choosing the Right VPN: Selecting a VPN service can be daunting due to the plethora of options available. Factors such as the level of encryption, server locations, speed, and customer support should be considered. It’s also important to evaluate the privacy policies of VPN providers to ensure they do not log user data, which could potentially compromise anonymity.
Common Misconceptions: There is a common belief that using a VPN makes one completely invisible online. While VPNs significantly enhance privacy and security, they are not infallible. Users should be aware of potential limitations and vulnerabilities, such as the possibility of VPN providers themselves being compromised or the existence of advanced tracking techniques that can bypass VPNs.
In conclusion, while VPNs are powerful tools for enhancing internet privacy and security, understanding their capabilities and limitations is essential. By carefully selecting a VPN service and being aware of best practices, users can significantly bolster their online security and privacy.
Protecting Against Phishing and Social Engineering
In this section, we delve into the sophisticated methods employed by malicious actors to deceive individuals and organizations. The primary focus is on understanding and mitigating the risks associated with phishing and social engineering tactics, which are designed to exploit human psychology for unauthorized access or financial gain.
Phishing involves fraudulent attempts to obtain sensitive information such as usernames, passwords, and credit card details by disguising as a trustworthy entity in electronic communications. Social engineering, on the other hand, leverages psychological manipulation to trick users into making security mistakes or giving away confidential information.
- Recognizing Phishing Attempts: Learn to identify common signs of phishing emails, such as poor grammar, suspicious URLs, and requests for immediate action.
- Educating Users: Implement comprehensive training programs to educate employees and individuals about the latest phishing techniques and how to respond appropriately.
- Using Anti-Phishing Tools: Deploy advanced software solutions that can detect and block phishing attempts before they reach the user.
Social engineering attacks often involve pretexting, baiting, or tailgating. Here are some strategies to defend against these tactics:
- Enhancing Awareness: Regularly update your knowledge about the latest social engineering scams and share this information with your team.
- Implementing Strict Access Controls: Use multi-factor authentication and enforce strict access policies to sensitive areas and information.
- Conducting Regular Audits: Perform security audits to identify vulnerabilities in your security protocols that could be exploited through social engineering.
By understanding these threats and implementing robust countermeasures, organizations can significantly reduce their vulnerability to these deceptive practices. Continuous education and vigilance are key in maintaining a secure environment against phishing and social engineering attacks.
The Future of Biometric Security Measures
In this section, we delve into the evolving landscape of biometric technologies and their role in enhancing personal identification and protection. As we progress into an era where data protection is paramount, these advanced methods offer a promising solution to traditional security challenges.
Evaluating Privacy Policies for Online Services
As the reliance on digital platforms continues to grow, understanding and evaluating the privacy policies of these services becomes increasingly crucial. Privacy policies outline how a service collects, uses, and protects user data. It is essential for users to be aware of these terms to ensure their personal information is handled responsibly.
Firstly, it is important to recognize what elements are typically included in a privacy policy. These documents generally detail the types of data collected, the purposes for which it is used, and the measures taken to secure this information. Additionally, they often specify the circumstances under which data might be shared with third parties.
When assessing a privacy policy, users should look for clarity and transparency. A well-written policy will be easy to understand and will not contain ambiguous language. It should clearly state the rights of the user regarding their data, including the right to access, modify, or delete their information.
Furthermore, users should be vigilant about the frequency of updates to these policies. Companies often revise their policies to adapt to new regulations or to change their data handling practices. Regularly reviewing these updates can help users stay informed about how their data is being managed.
In conclusion, while biometric security measures offer enhanced protection, it is equally important to critically evaluate the privacy policies of the services we use. This proactive approach ensures that our data remains secure and that our rights as users are respected.
Evaluating Privacy Policies for Online Services
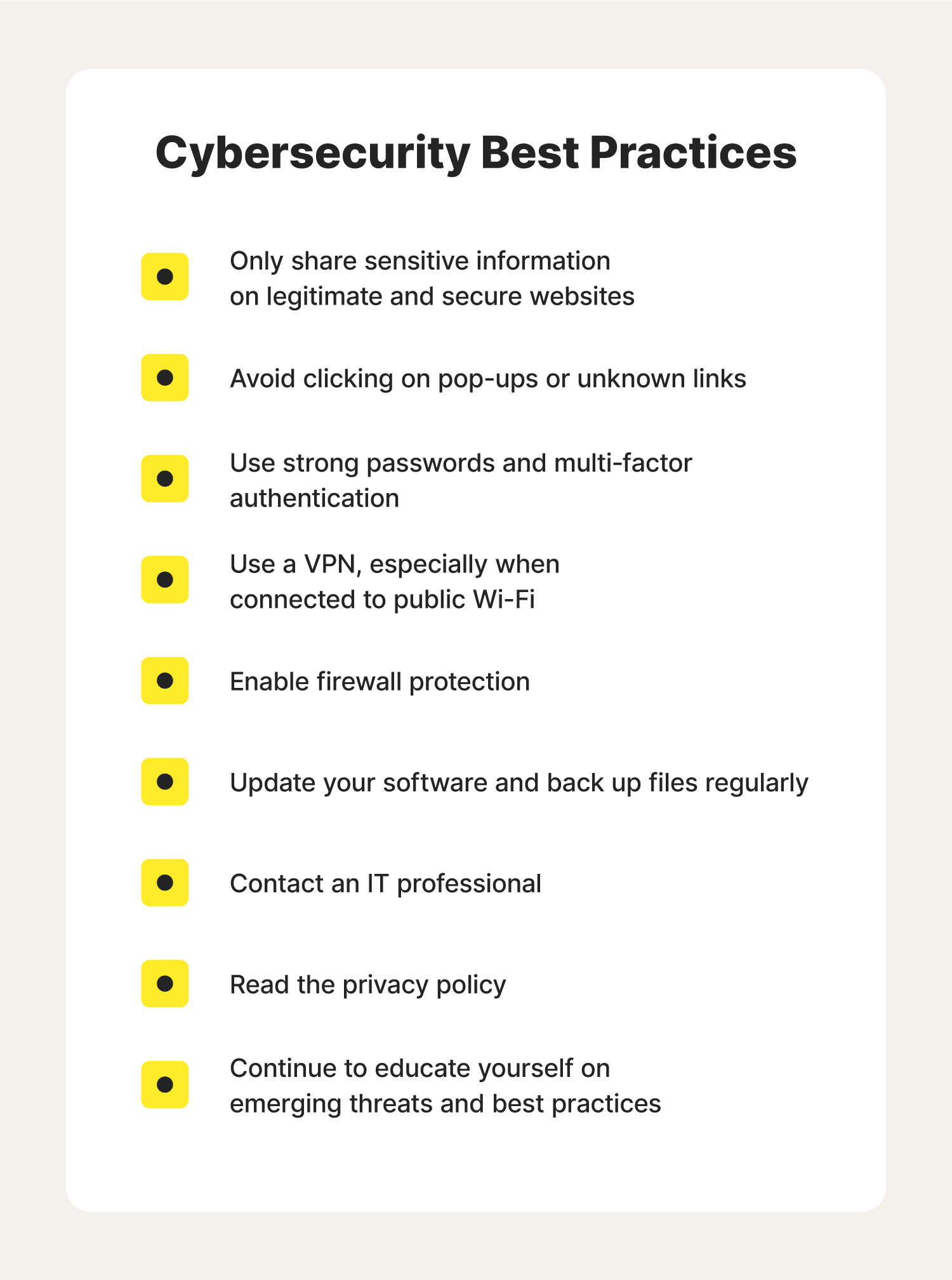
In this section, we delve into the critical task of scrutinizing the terms that govern the use of various web-based platforms. Understanding these documents is essential for safeguarding personal information and ensuring that one’s data is handled responsibly by service providers.
Why Review Privacy Policies?
Privacy policies are legal documents that outline how a company collects, uses, maintains, and discloses information from users. By thoroughly examining these policies, individuals can gain insight into the extent of data collection and the purposes for which their information might be utilized. This knowledge empowers users to make informed decisions about which services to trust with their personal details.
Key Elements to Look for in Privacy Policies
When evaluating a privacy policy, several key elements should be considered:
- Data Collection Practices: Understand what types of information are gathered (e.g., contact details, browsing history, etc.).
- Use of Data: Determine how the collected information is used, including whether it is shared with third parties or used for marketing purposes.
- Data Security Measures: Check what security protocols are in place to protect user data from unauthorized access or breaches.
- User Rights: Look for provisions that allow users to access, modify, or delete their personal information.
- Changes to Policy: Be aware of how and when the policy can be updated, and how users are notified of these changes.
Practical Steps for Evaluating Privacy Policies
To effectively review a privacy policy, follow these steps:
- Read the policy in its entirety to grasp the full scope of the company’s data practices.
- Compare the policy with those of similar services to identify any significant differences in data handling.
- Use online tools or resources that help simplify and summarize privacy policies, making them more accessible.
- Consider seeking legal advice if the policy is particularly complex or if you handle sensitive data.
By taking these steps, users can better protect their personal information and make more informed choices about the online services they use.
